What is Active Directory?
As someone working their way toward becoming a junior pentester, you’ll frequently come across Active Directory (AD)—whether it’s in a fresh 0-day vulnerability that’s all over forums and social media, or while practicing by solving Windows machines in HackTheBox. So, what exactly is Active Directory? To understand its significance, we need to take a step back to the 1990s, when businesses were transitioning from standalone systems to client-server architectures. This shift led to an increasing need for organizations to efficiently manage growing numbers of users, computers, and shared resources connected to their networks.
Microsoft seized this opportunity and introduced a distributed, hierarchical structure known as Active Directory, which allows for centralized management of an organization’s resources. AD organizes objects, such as users, computers, and shared resources, into organizational units (OUs). It also simplifies security by grouping users into security groups that can be managed and assigned permissions. These OUs and groups are themselves objects stored within the directory service.
Once Active Directory was released, organizations were thrilled by how much simpler the process of administering their resources had become. As a result, AD quickly became the go-to solution, and adoption soared. However, as the saying goes, “Every rose has its thorn.” Active Directory, while revolutionary, also introduced some significant risks. For example, even a basic user with no special privileges can enumerate most objects within AD. This creates an opportunity for attackers to map out an organization’s entire network, helping them build a plan for lateral movement and privilege escalation, potentially compromising a company’s network either partially or fully.
Today, Active Directory is one of the most critical components of IT infrastructures in organizations worldwide. It serves as the backbone for user authentication and authorization across networks. However, because it controls access to so many systems and resources, it has also become a primary target for bad actors. Understanding Active Directory and its vulnerabilities is essential for any penetration tester, as it can be the key to compromising an entire network.
The Active Directory Lingo
Before diving into advanced techniques for attacking Active Directory, such as Kerberoasting, NTLM relay attacks, and DACL attacks, it’s essential to build a strong foundation in the fundamentals of Active Directory. Understanding its structure, the protocols it relies on, and how it operates will allow us to make a smooth transition from being a beginner to becoming a proficient junior pentester or red teamer. This solid grasp of AD will ensure that we don’t fall into the trap of being a script kiddie, simply copy-pasting commands from tools like BloodHound, but instead, we’ll have the knowledge to understand the vulnerabilities we’re exploiting and the ability to think critically and creatively when assessing AD environments.
Active Directory Structure
Let’s begin by understanding the basic structure of Active Directory, its core members, and the fundamental concepts it was built upon, such as domains, users, and computers. These concepts formed the foundation of AD when it was first introduced. Over time, as organizations scaled and the number of devices and resources connected to the network exploded, Microsoft introduced additional features to handle this growth. These include forests, trees, and services, which were designed to provide more flexibility, security, and manageability in large enterprise environments.
Schema
A schema in Active Directory (AD) is similar to a schema in Database Management Systems (DBMSs) or a class in Object-Oriented Programming (OOP). It serves as a blueprint for the AD environment, defining the types of objects that can exist within the AD database and their associated attributes. This schema allows for the creation of objects based on predefined templates, automatically assigning default attributes to new objects upon creation, which helps streamline administrative tasks. For example, you can define a User schema to standardize the creation of new user accounts for employees, ensuring that each account has the necessary attributes such as usernames, passwords, and group memberships.
Domains and Domain names
In the context of Active Directory, a domain is a set of connected computers that share a common Active Directory database, which is managed by central servers called Domain Controllers (DCs). Each Domain Controller is identified by an IP address and a corresponding DNS name, which points to the Domain Controller but does not directly represent the domain it manages.
A domain name acts as the high-level identifier for the network resources managed by the Domain Controllers. To maintain consistency, many companies align their domain names with their website names or brand. For example, if a company’s website is frenzy.com, their internal domain name might be something like
FRENZY.LOCAL, while specific Domain Controllers could have DNS names likehr.frenzy.localandit.frenzy.local, indicating the specific server handling the domain but not necessarily representing the entire domain or subdomain hierarchy.
frenzy.local
|
.----------------'----------------.
| |
it.frenzy.local hr.frenzy.local
|
|
|
.---------'--------------.
| |
devs.it.frenzy.local sec.it.frenzy.localDomain Controllers
Domain Controllers are essentially the brains of an AD network. They handle authentication requests, verify users on the network, and control who can access the various resources in the domain. All access requests are validated via the domain controller and privileged access requests are based on predetermined roles assigned to users. It also enforces security policies and stores information about every other object in the domain.
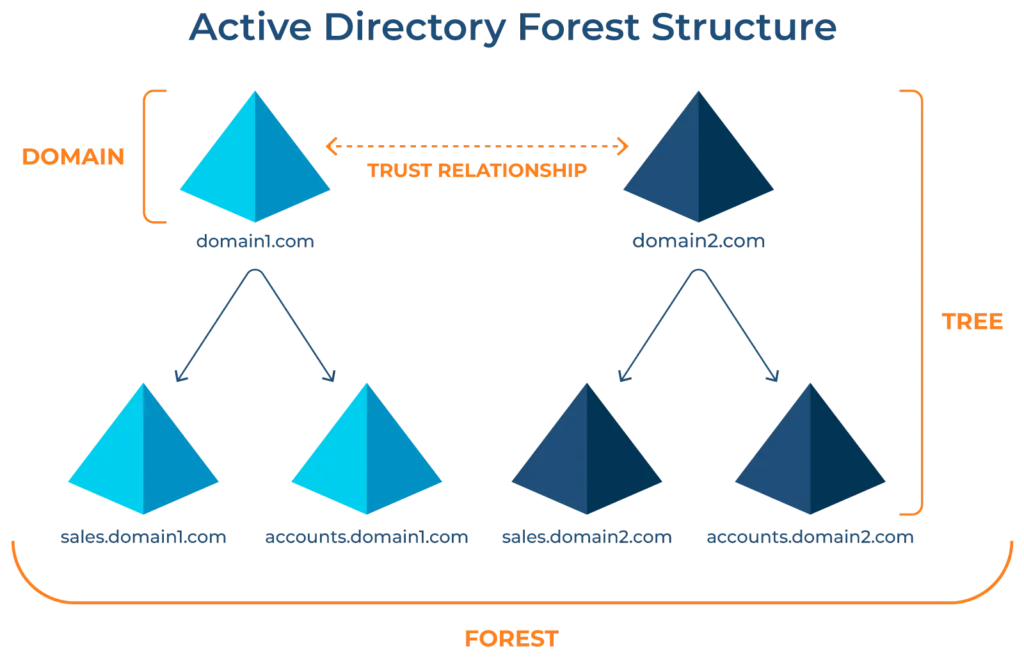
Tree
A tree in Active Directory is a collection of domains (e.g., devs.it.frenzy.local, sec.it.frenzy.local) that are organized under a single root domain (e.g., it.frenzy.local). Each domain within a tree shares a common namespace (e.g., it.frenzy.local) and is connected hierarchically. A parent-child trust relationship is automatically established when a domain is added under another domain in the tree, ensuring seamless communication and resource access between the domains. Additionally, all domains within the tree share the same schema and configuration, which guarantees consistency in the objects and attributes across the tree.
This hierarchical structure allows for a simplified, organized approach to managing resources and users across different domains. However, as organizations grow, they may need to span multiple trees, and this is where forests come into play.
Forest
A forest is a broader concept that allows for the logical grouping of multiple trees, potentially across different namespaces. For example, one tree might have the namespace it.frenzy.local, while another might use hr.frenzy.com. Despite these different namespaces, the forest ensures that all domains within it can still share a common schema, allowing for efficient management and interaction across various trees. Within the network, each forest operates independently but may have various trust relationships with other forests, enabling communication and resource sharing between them.
Foreign Security Principals
A foreign security principal (FSP) is an object created in AD to represent a security principal that belongs to a trusted external forest. They are created when an object such as a user, group, or computer from an external (outside of the current) forest is added to a group in the current domain.
Leaf
A leaf in Active Directory is the smallest unit in the directory hierarchy. Unlike domains, trees, and forests, which help organize multiple objects, a leaf is an individual object that cannot contain other objects within it.
Trusts
To fully leverage the Active Directory environment, trusts were introduced. A trust is a connection between domains that allows users in one domain to access resources in another domain, typically within the same forest. While you may be able to reach computers in other domains, a trust allows you to authenticate and gain access to resources in those domains using your credentials from the trusted domain, provided the proper permissions are granted. For example, if you’re in the IT domain and need to fix a computer in the HR domain, a trust lets you authenticate with your IT credentials and access the HR computer, assuming you have the right permissions. This enables users to seamlessly access resources across domains, promoting cross-domain functionality while maintaining security and separation between the domains.
Trust Directions:
Trusts can be configured to be either unidirectional or bidirectional:
One-way Trust: In this type of trust, one domain (the trusting domain) allows users from another domain (the trusted domain) to authenticate and access resources in the trusting domain. However, the reverse is not true. Users from the trusting domain cannot authenticate in the trusted domain.Two-way Trust: In this type of trust,both domains trust each other. This allows users from either domain to authenticate and access resources in the other domain, provided they have the necessary permissions. It establishesmutual trustbetween both domains.
Trust Types:
Trusts in Active Directory can be classified into several types, each with specific use cases:
External Trust: An external trust is used toestablish a trust relationshipbetween adomain in one forest and a domain in another forest. This type of trust is typically used when connecting non-AD domains or when resources in different forests need to be accessed.Forest Trust: A forest trust allows fora trust relationship between two forests, enabling users in one forest to access resources in another forest. Forest trusts are used when organizations have multiple forests and need to share resources across them.Realm Trust: A realm trust is used toestablish a trust relationship between an Active Directory domain and a non-Windows Kerberos realm, such as UNIX-based systems or other systems that support the Kerberos protocol. This trust type is typically used for environments where non-Windows systems are involved.Shortcut Trust: A shortcut trust isa direct trust relationship created between two domains in the same forest to speed up the authentication process. It is typically used in large forests with multiple domains, where establishing direct communication between distant domains is required to improve performance.Parent-Child Trust: A parent-child trust isthe default trust relationship automatically created when a child domain is added under a parent domain in a domain tree. This type of trust allows users and resources in the child domain to access resources in the parent domain, and vice versa, ensuring seamless communication between them.Forest Trust: A forest trust is atransitive trust between two forest root domains.
While trusts are powerful and enable seamless cross-domain functionality, misconfiguring them can introduce
serious security risks. Some notable attacks that can result frommisconfigured trustsinclude Forging Kerberos Trust Tickets for Spoofing Attacks and Sid-History Injection Attacks
NTDS.DIT - The heart of Active Directory
NTDS.DIT (New Technology Directory Service Database) is the Active Directory database file in Windows domain controllers (DCs). It contains all user accounts, passwords (hashed), group policies, and directory information. If an attacker gets access to ntds.dit, they can fully compromise an entire Active Directory environment.
Active Directory Objects
Users
Users are considered leaf objects in Active Directory, meaning they cannot contain any other objects within them. Each user object has numerous attributes, such as display name, last login time, date of last password change, email address, account description, manager, and address. These attributes helpdefine the identity and permissions of the user within the directory. User objects can represent anything from an employee’s account to a service account used by applications or automated processes. They are a crucial target for attackers, as gaining access to even a low-privileged user account can provide entry into the network, allowing access to various objects and resources and enabling detailed enumeration of the entire domain or even the entire forest.
User Secrets
In Active Directory, user secrets typically refer to sensitive information associated with a user account, such as their password, Kerberos tickets, NTLM hashes, or authentication tokens. These secrets are crucial for verifying a user’s identity and granting access to domain resources. When an attacker compromises user secrets, they can impersonate the user, escalate privileges, or gain unauthorized access to systems and data. User secrets are often targeted in penetration testing and attacks, as obtaining them can lead to broader network compromise, lateral movement, and access to sensitive information within the domain.
LM/NT hashes
LM and NT hashes are password representations stored in the SAM database on Windows machines or NTDS in Active Directory. The LM hash is outdated and considered weak, as it is easily cracked due to its simplified algorithm. Modern systems no longer use LM hashes, though they may still be stored for compatibility with older systems. The NT hash is stronger and used in current authentication, but it is still vulnerable to Pass-the-Hash (PTH) attacks, where attackers can steal the hash and use it to authenticate across systems, enabling lateral movement and privilege escalation without needing the plaintext password.
Security Identifiers SID VS. RID:
A security identifier is used to uniquely identify a security principal or security group. Security principals can represent any entity that can be authenticated by the operating system, such as a user account, a computer account, or a thread or process that runs in the security context of a user or computer account.
Users refer to accounts by the account name, but the operating system internally refers to accounts and processes that run in the security context of the account by using their SIDs. For domain accounts, the SID of a security principal is created by concatenating the SID of the domain with a relative identifier (RID) for the account. SIDs are unique within their scope (domain or local), and they’re never reused.
If we take this example:
User Name SID
==================== ============================================
cicada\administrator S-1-5-21-917908876-1423158569-3159038727-500The SID is S-1-5-21-917908876-1423158569-3159038727-500, meanwhile the RID is the last part of it which is 500.
Kerberos Keys
Kerberos keys are used in the Kerberos authentication protocol, which is widely used in Active Directory environments to authenticate users and services. These keys are derived from user passwords and are used to encrypt and decrypt tickets that prove a user’s identity within the network. If an attacker gains access to Kerberos keys, they can forge Ticket Granting Tickets (TGTs) or service tickets, allowing them to impersonate users or services and gain unauthorized access.
Computers
A computer object in Active Directory refers to any machine that is joined to the AD network, including servers, workstations, or even devices like printers. Computers are classified as leaf objects because they do not contain other objects. Despite this, they are considered security principals, meaning they have their own SID (Security Identifier) and GUID (Globally Unique Identifier).
While
user objectsare linked to human access,computer objectsare used to manage and control machine access, such as access to a shared server for data retrieval or to a printer for printing.
Groups
A group is considered a container object because it can contain other objects, including users, computers, and even other groups. A group IS regarded as a security principal and has a SID and a GUID. In AD, groups are a way to manage user permissions and access to other securable objects (both users and computers).
Group Unique Identifier GUID
A GUID is a unique 128-bit value assigned when a domain user or group is created. This GUID value is unique across the Active Directory, similar to a MAC address. Every single object created by Active Directory is assigned a GUID, not only user and group objects. The GUID is stored in the ObjectGUID attribute.
Group Policy Object GPO
Group Policy Objects are virtual collections of policy settings. Each GPO has a unique GUID. A GPO can contain local file system settings or Active Directory settings. GPO settings can be applied to both user and computer objects. They can be applied to all users and computers within the domain or defined more granularly at the OU level.
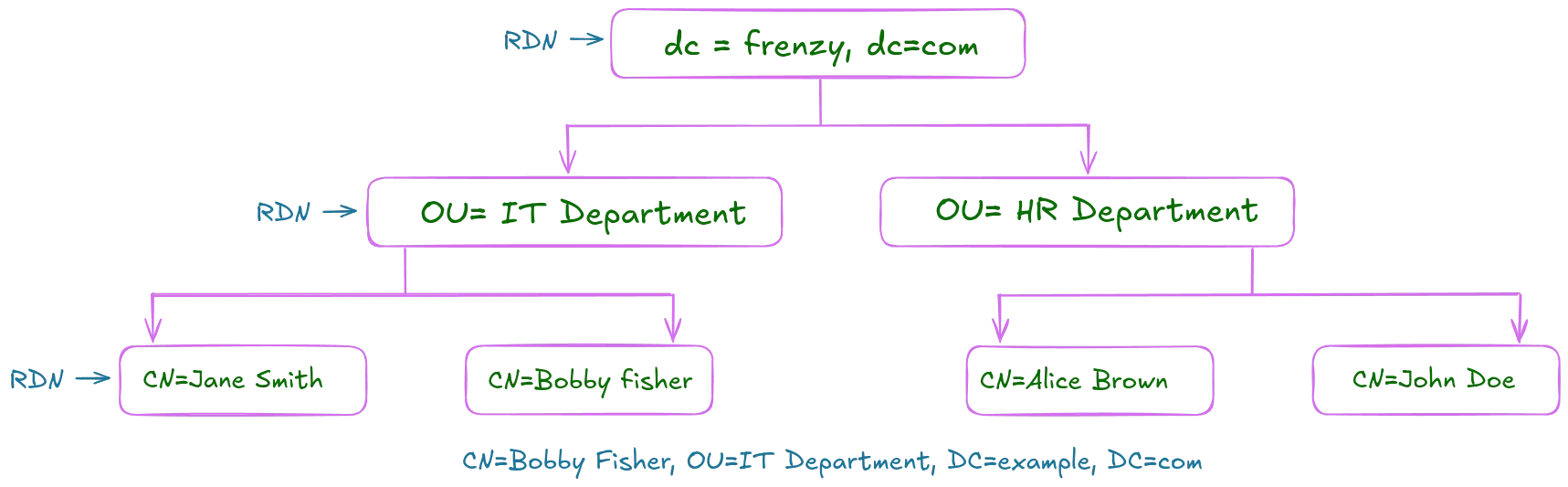
Distinguished Name VS. Relative Distinguished Name
- Distinguished Name
DN: The full path of an object in Active Directory, uniquely identifying it within the directory.- Example:
CN=bobby fisher,OU=IT,DC=frenzy,DC=com
- Example:
- Relative Distinguished Name
RDN: Theportion of a DNthat uniquely identifies an object within its parent container.- Example:
CN=bobby fisher(withinOU=IT,DC=frenzy,DC=com)
- Example:
Services
Active Directory services are essential components that enable authentication, authorization, and management of resources within a Windows domain. Key services include Domain Controllers (DCs) for user authentication, DNS for domain name resolution, and Global Catalogs (GCs) for searching the directory. Gaining control of Domain Controllers or manipulating DNS can allow attackers to escalate privileges, impersonate users, and compromise domain-wide security, making AD services critical to defend against during penetration testing and real-world attacks.
Service Principal Name SPN
A Service Principal Name uniquely identifies a service instance. They are used by Kerberos authentication to associate an instance of a service with a logon account, allowing a client application to request the service to authenticate an account without needing to know the account name.
MSSQLSvc/SQLSERVER01:1433
MSSQLSvc/SQLSERVER01.frenzy.com:1433Shares
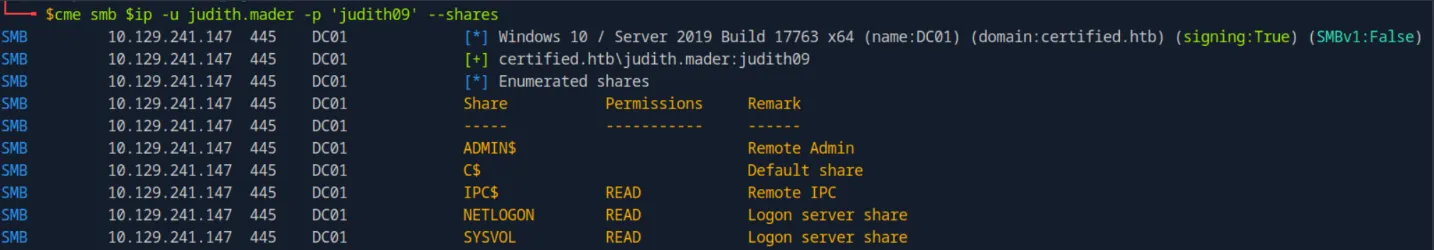
Shares in Active Directory refer to network resources such as files, folders, and printers that are made accessible to users and computers within the domain. Shared resources are typically managed by setting permissions to control who can read, write, or modify the shared data. In penetration testing environments, common SMB shares include ADMIN$, C$, IPC$, and NETLOGON, which provide access to administrative and system resources. Shares like NETLOGON and SYSVOL are often used to generate data for tools like BloodHound, as they can provide valuable information about group memberships, domain controllers, and privilege escalation paths within the network.
Organizational Units (OUs)
An Organizational Unit (OU) is a container used by system administrators to group similar objects for easier management. OUs allow for the delegation of administrative tasks without granting full administrative rights. For example, an Employees OU might contain child OUs for different departments like Marketing, HR, Finance, and Help Desk. If a user is granted the right to reset passwords at the top-level OU, they would have the ability to reset passwords for all users in the organization. However, by structuring OUs hierarchically, such as placing departments under the Help Desk OU, specific users within those child OUs can be delegated rights (e.g., password resets) for only their scope. Other administrative tasks that can be delegated at the OU level include creating or deleting users, managing group memberships, configuring Group Policy links, and resetting passwords.
Conclusion
Throughout this article, we’ve laid the foundation by covering essential Active Directory concepts and terminology crucial for pentesters and red teamers. But this is just the beginning. In the upcoming blogs, we’ll dive deeper into the inner workings of key authentication mechanisms like Kerberos and LDAP, focusing on how to identify and exploit vulnerabilities for privilege escalation and system compromise. We’ll also explore how misconfigurations can enable attacks such as NTLM relay, trust exploitation, and DACL manipulation. Buckle up and join me on this journey as we level up and become true Active Directory experts 🖤.